The First Successful Malware For Mac
Last weekend saw the first ever successful hack attack on Apple Mac products, where users’ computers and data were targeted by ‘ransomware’. Customers of Apple Inc.
Were targeted by hackers in the first successful campaign against Mac computers. The type of software used in the attack is known as ‘ransomware’, researchers with told Reuters on Sunday. This name arises from the software’s method of capturing a user’s system or data and holding it ‘hostage’ until a ransom is paid, usually using a hard-to-trace digital currency. At this time an electronic key is provided to ‘unlock’ the user’s files or data.
Those who fail to cough up the funds in time might find their systems corrupted and data irrevocably lost., ‘security experts estimate that ransoms total hundreds of millions of dollars a year from such cyber criminals, who typically target users of Microsoft Corp’s Windows operating system (OS). Palo Alto Threat Intelligence Director Ryan Olsen said that the “KeRanger” malware, which appeared on Friday and ran rampant over the weekend, is the first functioning ransomware aimed at Apple’s Mac OS. 'This is the first one in the wild that is definitely functional, encrypts your files and seeks a ransom,'. KeRanger malware hid within Transmission's 2.90 installer The virus took hold of computers via a tainted copy of popular program Transmission, a BitTorrent peer-to-peer file sharing platform, Palo Alto said in a afternoon. Two installers of Transmission version 2.90 were infected with KeRanger on the morning of March 4th. As Transmission is an open source project, it is difficult to pinpoint the exact method of infection, but it is possible that Transmission’s official website was compromised and the files replaced by re-compiled malicious versions, though they do point out that they are unable to confirm this. The KeRanger application bypassed the Apple Gatekeeper protection as it was signed with a valid Mac app developer certificate.
The developed listed on the certificate is a Turkish company with a different developer ID to that used to sign previous versions of the Transmission installer. The corrupted installers were generated and signed on the morning of Marc h 4th, according to the code signing information. Once the infected apps are installed, an embedded.exe filed is run on the system, where it lurks for three days before connecting with command and control (C2) servers via the TOR anonymiser network.
The malware then begins encrypting certain types of document and data files on the system and, once finished, demands that victims pay one BitCoin (roughly £289) to a specific address, whereupon they will receive an electronic key to decrypt their files., the KeRanger malware appears to still be under active development and seems to be also attempting to encrypt ‘Time Machine’ backup files to prevent victims recovering their backup data. Since the ransomware was reported to the Transmission Project and Apple on March 4th by Palo Alto Networks, Apple have revoked the abused certificate and updated XProject antivirus signature, and the Transmission Project has removed the malicious installers from its website. CBSbutler's consultant wonders whether Apple's recent presence in the news regarding the FBI's request for a 'backdoor' into some of their hardware could have inspired this attack, the first to succeed against Apple's systems, and wonders whether the vulnerabilities that enabled this 'ransomware' to succeed could be applied to other Apple products, such as the iPhone. He will be watching with interest to see how Apple responds to this attack against their operating system, OS X, and whether a flurry of defensive updates are on their way. Our leader recalls that this is not, in fact, the first time that Apple have been targeted by hackers: hundreds of millions of iPhone and iPad users were when some of China's most popular apps were targeted by hackers, who convinced the legitimate developers to use fake Apple software in their builds. This is, however, the first time a ransomware attack has targeted Apple's Mac OS, and Alex thinks the corporation are to be commended for the speed with which they dealt with the threat, both in terms of detection and quick defensive actions to limit the number of users affected. This attack puts the cyber-security spotlight on Apple, as the technology community looks to see how they will counter future threats - a question of paramount importance to the tech giants of today.
Malware For Mac Free Download
Apple will also need to assess how this will damage their status of being untouched by virus concerns, and how they can repair the confidence damaged by this incident.
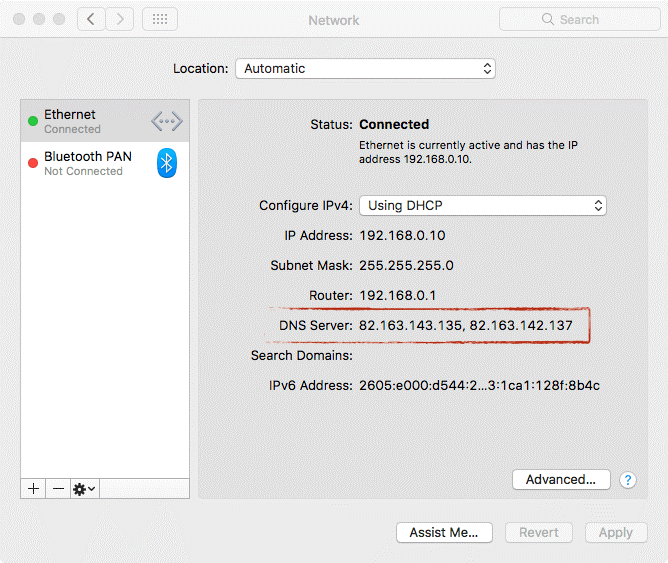
We are barely two weeks into 2018, and security researchers have already spotted the first new Mac malware strain this year. Called OSX/MaMi, all evidence points that this is still a work in progress, but one that comes with some pretty intrusive features, if ever completed and activated. The malware's first victim appears to be, who suspected a malware infection after realizing he/she couldn't change their Mac's DNS servers. MaMi comes with some pretty worrisome features Following some clever sleuthing, Mac security expert Patrick Wardle tracked down the malware hosted on a website located at regardens.info.
The malware is distributed in the form of an unsigned Mach-O 64-bit binary that currently doesn't trigger any detections on aggregated scan engines such as VirusTotal. Analyzing the malware source code, Wardle says he found code that hinted the malware could. ⯮ Install a local certificate ⯮ Set up custom DNS settings ⯮ Take screenshots ⯮ Hijack mouse clicks ⯮ Run AppleScripts ⯮ Get OS launch persistence ⯮ Download and upload files ⯮ Execute commands The current version of this malware does not support most of these features, but can only get boot persistence, install a local certificate, and set up custom DNS server settings. Taking into account the rest of the features, this could very well be a remote access trojan in the making, but currently, it can only be classified as a mere DNS hijacker. MaMi can evolve in the future 'OSX/MaMi isn't particular advanced - but does alter infected systems in rather nasty and persistent ways,'.
The First Successful Malware For Mac Mac
'By installing a new root certifcate and hijacking the DNS servers, the attackers can perform a variety of nefarious actions such as man-in-the-middle'ing traffic (perhaps to steal credentials, or inject ads).' But Wardle fears the malware could evolve pretty quick and might have more secrets hidden in its code.
'Perhaps in order for the more intrusive methods taking screenshots, executing commands to be executed or for the malware to be persisted, requires some attack-supplied input, or other preconditions that just weren't met in my VM. I'll keep digging!,' Wardle said. The two DNS servers the malware adds to infected hosts are: 82.163.143.135 82.163.142.137.